WazeHell Vulnerable AD Tutorial
TL;DR
After my Pentester Academy lab access expired, I still needed more practice before I could attempt the exam. I had only purchased 30 days and although I had gone through every concept, I still needed to drill everything down. A friend had suggested I set up a vulnerable AD lab, from this link, but I could not find a tutorial on how to set it up anywhere. The lab is pretty comprehensive, but for a beginner, a bunch of scripts can be pretty confusing. So I decided to write this, for anyone needing help.
Prerequisites
- You need to have a Windows server running in VBox or Vmware. I had a Windows Server 2019 set up in VMware. I already had an AD set up on this.
- If you don’t have AD set up, that’s okay too. You can follow the videos from TCM academy that I have linked here.
- If you only have a server without an AD in your VM, and you don’t want to set up the AD manually, you can set it up using the following script from WazeHell’s README.
Install-ADDSForest -CreateDnsDelegation:$false -DatabasePath "C:\\Windows\\NTDS" -DomainMode "7" -DomainName "cs.org" -DomainNetbiosName "cs" -ForestMode "7" -InstallDns:$true -LogPath "C:\\Windows\\NTDS" -NoRebootOnCompletion:$false -SysvolPath "C:\\Windows\\SYSVOL" -Force:$truePS: I’m not sure how well this works because I already had an AD set up.
Getting Started
I think the setup is pretty straightforward once you are done with it, but when you are facing errors it’s hard to find ways to resolve the errors. So I’m gonna provide a clear road for that.
- Login to your DC machine (mine is a Windows Server 2019)
- Open Powershell
- Run the following command
IEX((new-object net.webclient).downloadstring("https://raw.githubusercontent.com/wazehell/vulnerable-AD/master/vulnad.ps1"));This is to download the script from the Github repo.
4. You will most probably get this error when you first run the command.

This is caused by the banner function in the script. From reading the issues on the GitHub page, I found out that the function is not encoded properly and that is why it is spewing errors like that.
5. To resolve the error, clone the repo to your machine.
git clone https://github.com/WazeHell/vulnerable-AD.gitOpen the vulnad.ps1 script to edit it. Essentially all you have to do is delete the banner function and the script will work as expected.

As you can see in the picture, the highlighted lines are causing errors. Delete those and save the script.
6. Run the script. If you edited and saved the script saved on your DC you can run the following command:
. .\vulnad.ps1followed by:
Invoke-VulnAD -UsersLimit 100 -DomainName "cs.org"Replace cs.org with the name of your Domain. Mine is alderson.local.
After that you should see the following output:
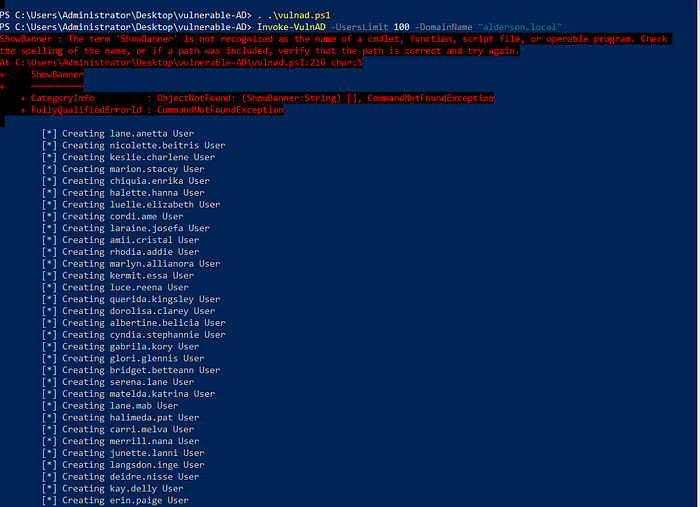

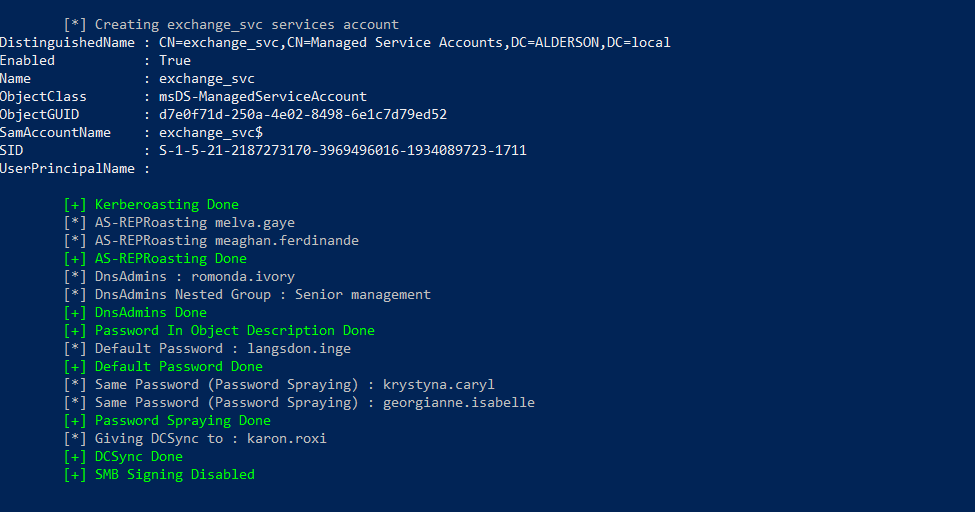
And you have successfully set up your vulnerable AD!
I hope this helps. Follow me on more content infosec-related, and don’t forget to clap if you managed to get to the end.
